This is a guide to extract the boot image from a cheap Android tablet based on Allwinner A133 using U-Boot (accessed via UART). The original firmware was not found on the internet. With the boot image and Magisk, you can root your Android tablet to make it more useful.
Pritom P7 is a very cheap Android tablet. I bought it for 33 USD from AliExpress, but it can be found for as low as 27 USD. This is a Google GMS-certified device (it passes Play Integrity, no malware was found when I received it), and it uses 32-bit Android Go. I am only using this to test some 32-bit Android app compatibility.
They may have several variants of this model with different specifications. Mine is: Alwinner A133, 1.5GB RAM (advertised as 2GB, and shown as 2GB in the Android info), 32 GB ROM, only 2.4 GHz WIFI, no GPS.
Unlockable Bootloader
Luckily, we are allowed to unlock the bootloader of this device using the developer menu, adb reboot bootloader then using fastboot oem unlock. Some cheap Android devices don’t allow unlocking (for example, the ones that are based on recent Unisoc SOC).
The product ID of my tablet is P7_EEA (Android 11) with kernel version Linux localhost 5.4.180-svn33409-ab20220924-092422 #28 SMP PREEMPT Sun Aug 20 19:13:45 CST 2023 armv8l. The build number is PRITOM_P7_EEA_20230820.

I did not find any Android exploit for this device, and I also didn’t find any backdoors. From my experience, some of these cheap Android devices have hidden su backdoors. Unable to find an exploit, I gave up trying to extract boot image from user space.
With some SOC, you can easily read/dump/extract the flash using PC software. I didn’t find any software for this Allwinner chip. An example of a SOC that allows flash reading is Unisoc (formerly Spreadtrum), but on the other hand, the bootloader on phones and tablets with the latest SOCs from Unisoc (that I know of) is not unlockable.
UART
Fortunately, this device is easy to open, and a UART pin is on the top left near the camera.
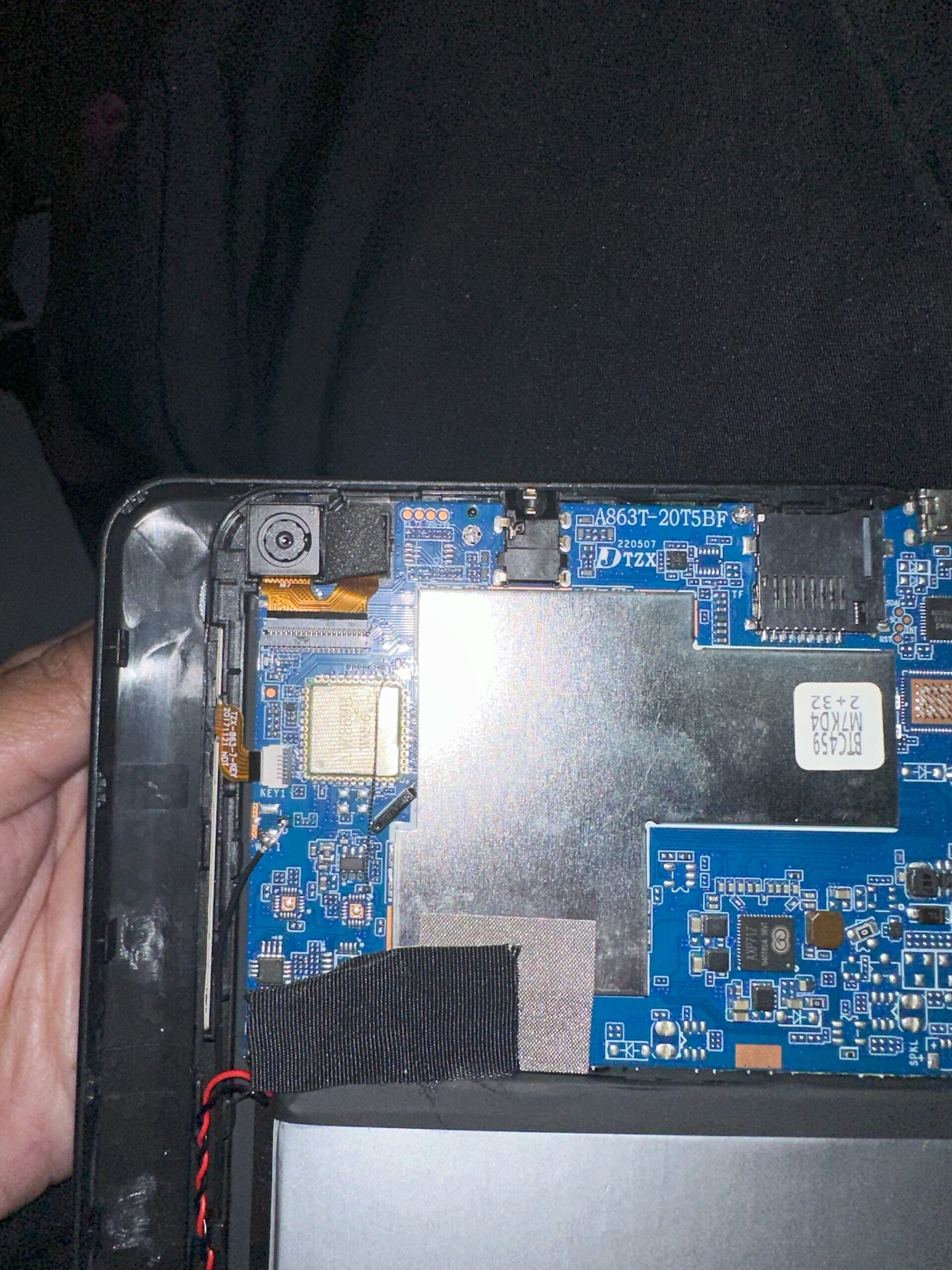
Here is a close-up:
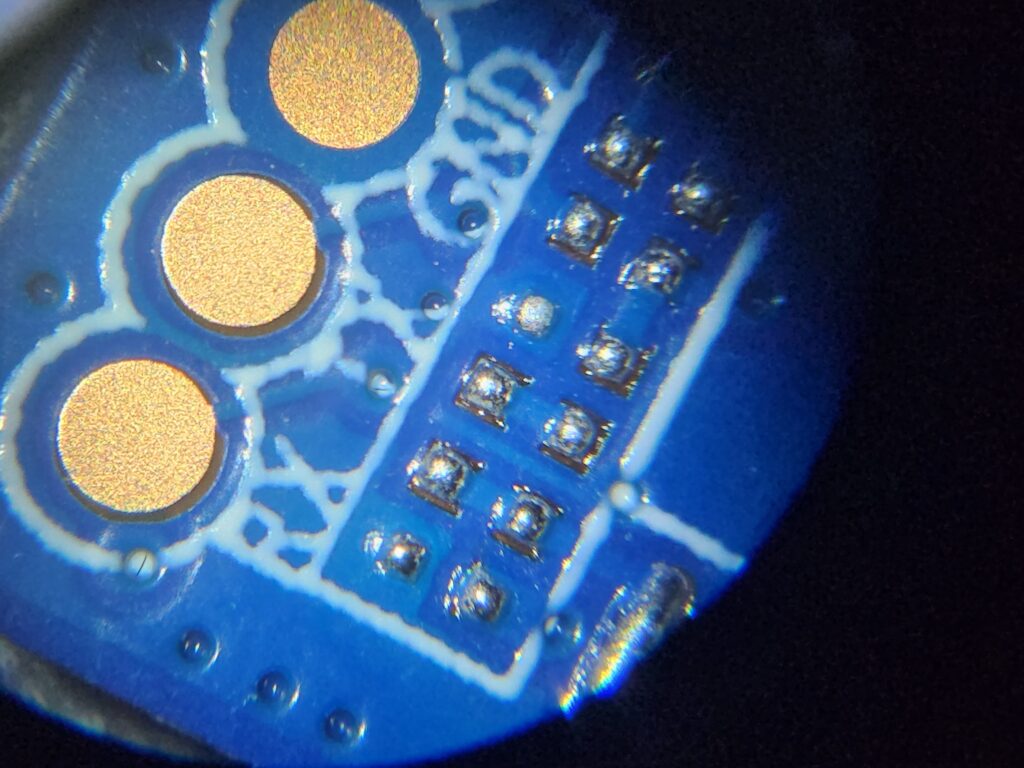
The right-most pin is FEL if you want to enter FEL mode. But entering FEL mode can be done easily using: adb reboot efex.
To test that the pin does output something, I just connected the ground to the USB-C ground and held my hand, pressing a cable on the TX pad during startup.

U-Boot
Fortunately, we can break into u-boot (not locked down); from there, it is easy to dump the bootloader. There are many ways to do it, but this is how I did it. First, print the environment using env print to see what commands are used to load the boot partition:
bootdelay=0
boot_normal=sunxi_flash read 45000000 boot;bootm 45000000
Note: I suggest you change the bootdelay to make it easier to enter U-boot next time.
We can see that we can read the flash partition to a certain memory location using:
sunxi_flash read 45000000 boot
Now, we need to write this memory area to an SD Card. I prepared a FAT-formatted SD Card. Insert it, then: sunxi_card0_probe. This will detect the card. I need to do mmcinfo otherwise, the next command won’t work:mmc part
Now we can test listing the content of the card: fatls mmc 0:1. It should be empty since we just format it. Next is to write the memory to a file: fatwrite mmc 0:1 45000000 boot.img 4000000. Note: all numbers are in hexadecimal. 64 Megabytes is just a common size for the boot partition.
We can install Magisk APK to the tablet, run it, and then choose “Install” and “Select and patch file”. Patch our boot.img, then the magisk_patched_xx.img file can be flashed using : fastboot flash boot magisk_patched_xx.img.
I could have dumped all the partitions using u-boot, but I felt that u-boot is slow in writing to the SD Card. After we have a root access, we can easily dump the rest of the partitions by accessing the files in /dev/block/by-name.
Conclusion
I hope this guide can help you root your Allwinner device, even when you don’t have the original firmware.
I think this device is not worth buying unless you have a specific need for it. This tablet is OK if you want to test your app for Android Go or 32-bit Android libraries. This is also a good tablet for learning to hack Android hardware.
If you are using the same device and want to have the boot partition, you can download it here: please make sure that your hardware is exactly the same as mine to prevent bricking it.
ivan@M16 ~ % fastboot devices
3c000c4543c48701e19 fastboot
ivan@M16 ~ % fastboot oem unlock
FAILED (remote: ‘Oem unlock ability is 0. Permission denied for this command!’)
fastboot: error: Command failed
Please help to unlock
Developer options – ON, OEM Unlocking – ON
(bootloader) treble-enabled:true
(bootloader) first-api-level:30
(bootloader) dynamic-partition:true
(bootloader) system-fingerprint:PRITOM/P7_A1/P7_A1:11/RP1A.201005.006/20220915-103124:user/release-keys
(bootloader) snapshot-update-status:none
(bootloader) super-partition-name:super
(bootloader) hw-revision:0
(bootloader) off-mode-charge:0
(bootloader) battery-voltage:0
(bootloader) is-userspace:yes
(bootloader) partition-type:bootloader_b:raw
(bootloader) partition-type:dtbo_a:raw
(bootloader) partition-type:vbmeta_vendor_b:raw
(bootloader) partition-type:vendor_boot_b:raw
(bootloader) partition-type:bootloader_a:raw
(bootloader) partition-type:vbmeta_system_b:raw
(bootloader) partition-type:userdata:raw
(bootloader) partition-type:env_b:raw
(bootloader) partition-type:boot_b:raw
(bootloader) partition-type:misc:raw
(bootloader) partition-type:dtbo_b:raw
(bootloader) partition-type:env_a:raw
(bootloader) partition-type:vendor_boot_a:raw
(bootloader) partition-type:vbmeta_b:raw
(bootloader) partition-type:vbmeta_a:raw
(bootloader) partition-type:vbmeta_system_a:raw
(bootloader) partition-type:media_data:raw
(bootloader) partition-type:vbmeta_vendor_a:raw
(bootloader) partition-type:boot_a:raw
(bootloader) partition-type:metadata:raw
(bootloader) partition-type:super:raw
(bootloader) partition-type:system_a:raw
(bootloader) partition-type:system_b:raw
(bootloader) partition-type:vendor_a:raw
(bootloader) partition-type:vendor_b:raw
(bootloader) partition-type:product_a:raw
(bootloader) partition-type:product_b:raw
(bootloader) secure:yes
(bootloader) battery-soc-ok:yes
(bootloader) serialno:3c000c4543c48701e19
(bootloader) slot-count:2
(bootloader) cpu-abi:armeabi-v7a
(bootloader) variant:NA
(bootloader) has-slot:bootloader:yes
(bootloader) has-slot:dtbo:yes
(bootloader) has-slot:vbmeta_vendor:yes
(bootloader) has-slot:vendor_boot:yes
(bootloader) has-slot:vbmeta_system:yes
(bootloader) has-slot:userdata:no
(bootloader) has-slot:env:yes
(bootloader) has-slot:boot:yes
(bootloader) has-slot:misc:no
(bootloader) has-slot:vbmeta:yes
(bootloader) has-slot:media_data:no
(bootloader) has-slot:metadata:no
(bootloader) has-slot:super:no
(bootloader) has-slot:system:yes
(bootloader) has-slot:vendor:yes
(bootloader) has-slot:product:yes
(bootloader) product:P7_A1
(bootloader) is-logical:bootloader_b:no
(bootloader) is-logical:dtbo_a:no
(bootloader) is-logical:vbmeta_vendor_b:no
(bootloader) is-logical:vendor_boot_b:no
(bootloader) is-logical:bootloader_a:no
(bootloader) is-logical:vbmeta_system_b:no
(bootloader) is-logical:userdata:no
(bootloader) is-logical:env_b:no
(bootloader) is-logical:boot_b:no
(bootloader) is-logical:misc:no
(bootloader) is-logical:dtbo_b:no
(bootloader) is-logical:env_a:no
(bootloader) is-logical:vendor_boot_a:no
(bootloader) is-logical:vbmeta_b:no
(bootloader) is-logical:vbmeta_a:no
(bootloader) is-logical:vbmeta_system_a:no
(bootloader) is-logical:media_data:no
(bootloader) is-logical:vbmeta_vendor_a:no
(bootloader) is-logical:boot_a:no
(bootloader) is-logical:metadata:no
(bootloader) is-logical:super:no
(bootloader) is-logical:system_a:yes
(bootloader) is-logical:system_b:yes
(bootloader) is-logical:vendor_a:yes
(bootloader) is-logical:vendor_b:yes
(bootloader) is-logical:product_a:yes
(bootloader) is-logical:product_b:yes
(bootloader) vendor-fingerprint:PRITOM/P7_A1/P7_A1:11/RP1A.201005.006/20220915-103124:user/release-keys
(bootloader) version-vndk:30
(bootloader) unlocked:no
(bootloader) current-slot:a
(bootloader) version-os:11
(bootloader) version-baseband:
(bootloader) max-download-size:0x10000000
(bootloader) partition-size:bootloader_b:0x2000000
(bootloader) partition-size:dtbo_a:0x200000
(bootloader) partition-size:vbmeta_vendor_b:0x10000
(bootloader) partition-size:vendor_boot_b:0x2000000
(bootloader) partition-size:bootloader_a:0x2000000
(bootloader) partition-size:vbmeta_system_b:0x10000
(bootloader) partition-size:userdata:0x67C77BE00
(bootloader) partition-size:env_b:0x40000
(bootloader) partition-size:boot_b:0x4000000
(bootloader) partition-size:misc:0x1000000
(bootloader) partition-size:dtbo_b:0x200000
(bootloader) partition-size:env_a:0x40000
(bootloader) partition-size:vendor_boot_a:0x2000000
(bootloader) partition-size:vbmeta_b:0x20000
(bootloader) partition-size:vbmeta_a:0x20000
(bootloader) partition-size:vbmeta_system_a:0x10000
(bootloader) partition-size:media_data:0x1000000
(bootloader) partition-size:vbmeta_vendor_a:0x10000
(bootloader) partition-size:boot_a:0x4000000
(bootloader) partition-size:metadata:0x1000000
(bootloader) partition-size:super:0xC0000000
(bootloader) partition-size:system_a:0x305EA000
(bootloader) partition-size:system_b:0x0
(bootloader) partition-size:vendor_a:0x4F91000
(bootloader) partition-size:vendor_b:0x0
(bootloader) partition-size:product_a:0x4822D000
(bootloader) partition-size:product_b:0x0
(bootloader) security-patch-level:2022-10-05
(bootloader) version-bootloader:unknown
(bootloader) version:0.4
Also I can’t flash your boot image
ivan@M16 ~ % fastboot flash boot /Volumes/Temp/pritom-P7_EEA-boot.img
Sending ‘boot_a’ (65536 KB) FAILED (remote: ‘Download is not allowed on locked devices’)
fastboot: error: Command failed
I think you are using a different device (not the same one as mine). So I am not sure what to do for your device.
I just bought one of these tablets, and they can be okay for a grandparent or a child (or for playing around with root or for 3D printer screen etc.). Your detailed description of the process has helped me a lot. I would like to say thank you to everyone who wants to play around with this tablet (I ordered mine for 33 euros, and it has the same specs as yours).
Oem Unlocking is on but when I try fastboot oem unlock:
oem unlock ability is 0. Permission denied for this command
Using the exact same model with the same build.
Oem unlocking option activated.
Can you help me?
C:\Users\Jardel>adb reboot fastboot
C:\Users\Jardel>fastboot oem unlock
FAILED (remote: ‘Oem unlock ability is 0. Permission denied for this command!’)
fastboot: error: Command failed
I guess in your particular model, the bootloader is forever locked? or may be try different fastboot binary, may be a newer or older version of it.
I was able to root my Pritom P7 EEA using this method. Thanks a bunch for extracting the boot image 😀
Hi, I’m trying to do the same boot.img extraction process on another similar tablet powered by the same SoC. The problem is that I’m new to Uart and all of that stuff and I don’t understand where to run the commands for the dumping process. Here’s what I already done: unlocked my bootloader and checked for su binary but no luck there. Opened up the tablet and located the TX and RX pins on the mobo, soldered wires there and connected them to my Uart adapter (CP2102 if that matters) including the ground taken from the USB-C port and then it was the part where I have no idea what to do next, turning the tablet on lights up one of the LEDs on my adapter and then it starts blinking during startup. I tried using putty on my windows pc to connect to the adapter but when I start a session I see nothing, even when pressing the reset button or doing anything else its just a blank terminal. If you can give me some advice on what to do next or provide some links where it explains a similar process more datelined it would be great. Thank you in advice!
Make sure you connect RX to TX and TX to RX and make sure you choose the correct baud rate.
Thanks a lot for your response, I swapped around the wires and tried different baud rates (11500 seems to be working fine) and now I see logs as I hit the reset button and during the boot process. Now I tried “adb reboot efex” and it kinda worked (the tablet rebooted and now I have a black screen and in my console I see some U-boot welcome messages and that stuff so I guess that its working fine) but I still can’t type anything to the console window on my pc, I’m guessing I might need a different app or something to be able to run commands. Would really appreciate it if you can share the app you used to run the commands.
So a small update on that, I was able to type commands after just pressing one button on my keyboard during the tablet’s boot process, I ran all of the commands and got my boot image but magisk is unable to patch it for some reason, maybe the size is not the same as on ur device but in U-boot when I type “env print” I get the same normal boot string as yours “boot_normal=sunxi_flash read 45000000 boot;bootm 45000000” and in fastbootd when I type “getvar all” I get “(bootloader) partition-size:boot_a:0x4000000” and “(bootloader) partition-size:boot_b:0x4000000” so I guess the command “fatwrite mmc 0:1 45000000 boot.img 4000000” should be the same for me? As I said I get an error when truing to patch the image saved to the SD card and it says that “Unable to patch ramdisk” but another thing is that it says “Magisk patched boot image detected” while the image is definitely wasn’t patched with magisk before. Maybe its because my SD card is in Fat32 and not just Fat but idk doesn’t seem like it complains about that during the dump process in U-boot.
Did you do “sunxi_flash read 45000000 boot” before writing to MMC? This will read the boot loader to memory before you write it to disk.
So I think the issue was in my SD card, I tried a different one and it finally worked. btw I spend like 4 hours yesterday trying to understand what was wrong and went as far as comparing ur image with mine in hex editor and only then I saw that it was weird (I mean hex is always a weird for me but it just looked really corrupted). I want to thank you for all the afford u put into troubleshooting it for me, I learned a lot of new stuff and I think that’s gonna be really useful in my adventures of yanking random crappy tablets for fun
I am glad it works for you. This is how I started: by just trying to follow some random stuff made by someone else on the internet.
Now with root installed, how do I backup the recovery?
in dev/block/by-name there is no recovery folder
it doesn’t have a recovery partition, it just uses boot_a and boot_b